Protect your data with advanced security
Jicoo secures data with a secure system certified by an external agency audit and advanced administrative features such as ACLs.
Sign up is free. Get started now.
Certifications and frameworks
Certified by an external auditing organization (ISO 27001). We operate our services in accordance with data privacy guidelines.
Enterprise-grade security
Protection of Customer Data
Logical Tenant Separation
Encryption at-rest (AES-256) and in transit
Infrastructure Security
Served by leading cloud infrastructures
Network and Perimeter Protection
Application Protection
Web Application Firewall
Distributed Denial of Service (DDoS) attack countermeasures
Regular vulnerability scanning
Compliance & Privacy
CCPA compliance management
ISO/IEC 27001 (ISMS) certification
Organization Security
Security education and awareness training
24/7 monitoring and incident response
Vendor risk management
Implement a sustainable business plan
Account Protections
bot elimination
Real-time activity (audit) logs
Deletion management of PII
Flexible admin management
Safe and secure development and operation
The service is built to ensure safe and secure data connection and retention for both hosts and guests.
More confidence
Protected by SSL/SSL
All communications are encrypted using SSL/TLS. This protects the data being transmitted from being intercepted or tampered with, and allows you to use the service safely.
Encryption of stored data
Since the entire database is encrypted, the risk of reading or leaking data is minimized even in the event of unauthorized removal.
Periodic vulnerability testing
To prevent unauthorized access and information leakage, the system is regularly inspected for vulnerabilities.
Continuous monitoring of operating status
We constantly monitor the system operation status, external attacks, etc., and have a system in place to detect failures, etc., as soon as they occur.
Backup and failover
Backups are taken on a daily basis, and in the event of a failure, the system automatically fails over to ensure maximum availability.
Adapt to evolving business needs — without the risk
Scale-ready security
It has features to meet corporate security requirements, such as ACLs and real-time activity (audit) logs for teams with large numbers of employees.

Restrictions in the domain, data protection
Users registering with Jicoo can be restricted by email address domain, or uploaded in batches by the administrator
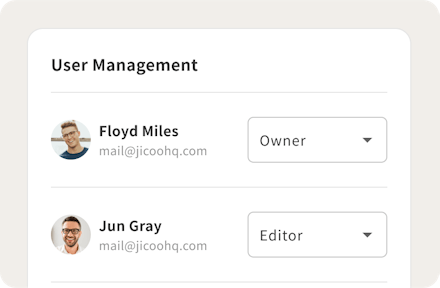
Access control for secure operation
Team members can be divided into administrators, members, and other privileges to manage team members, payments, and booking pages, preventing unauthorized changes.

Enterprise-ready data governance
Maintain compliance with advanced risk management features, including team-customizable terms of use and data deletion response
Terms & Policies
Resources such as conventions and policies related to security





